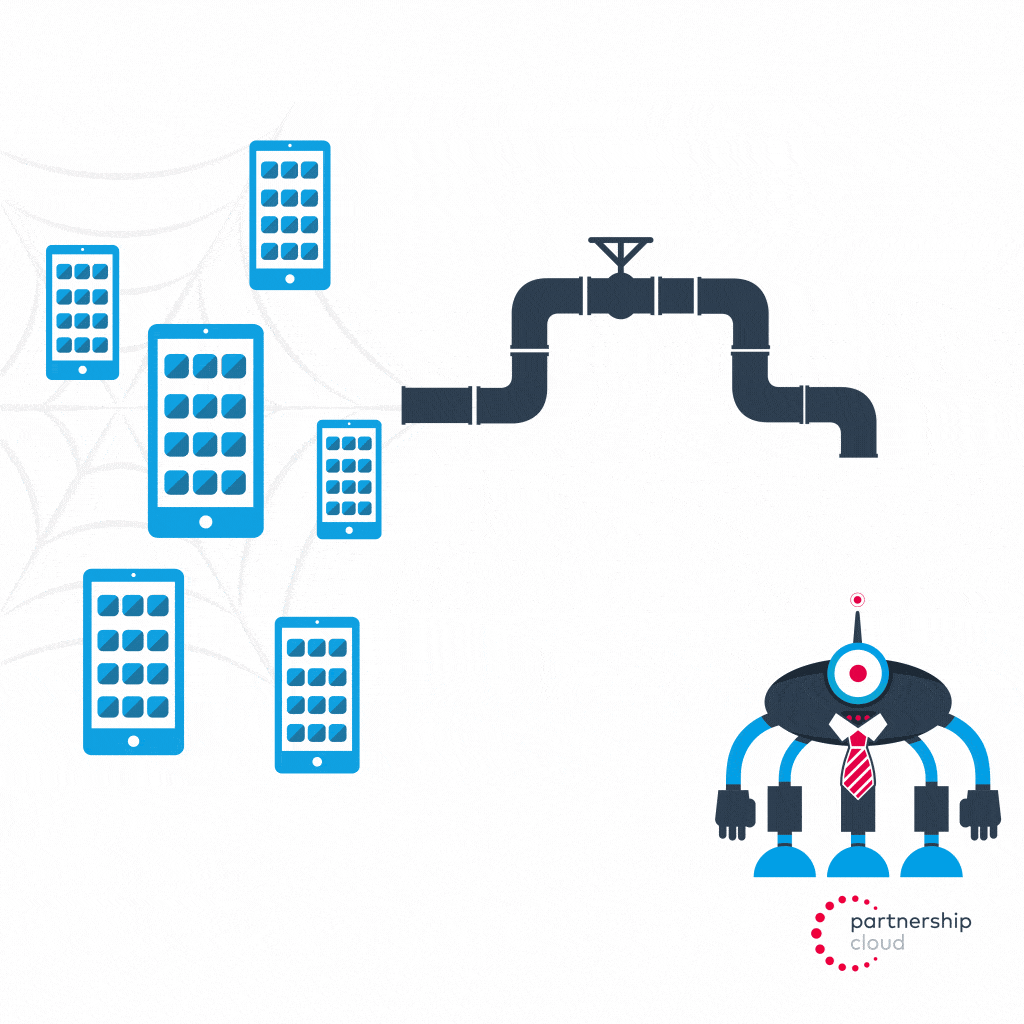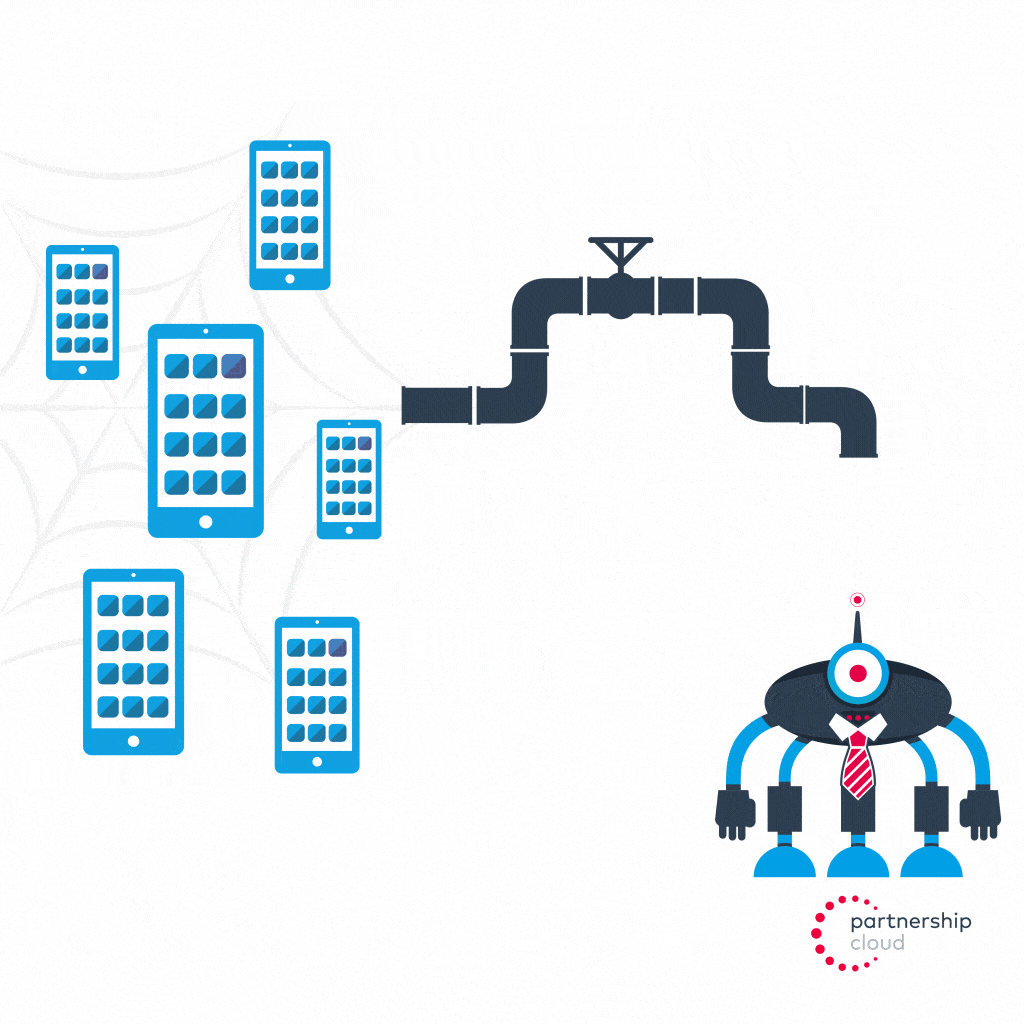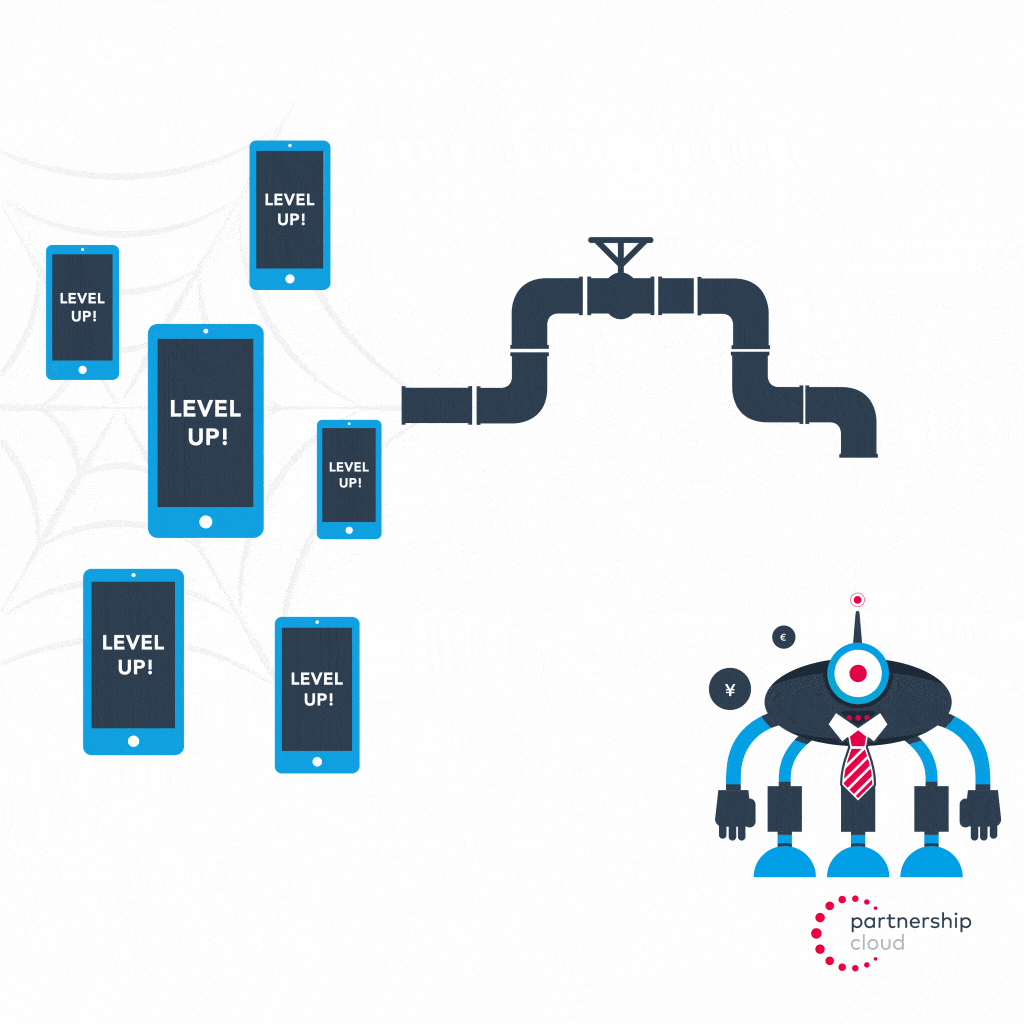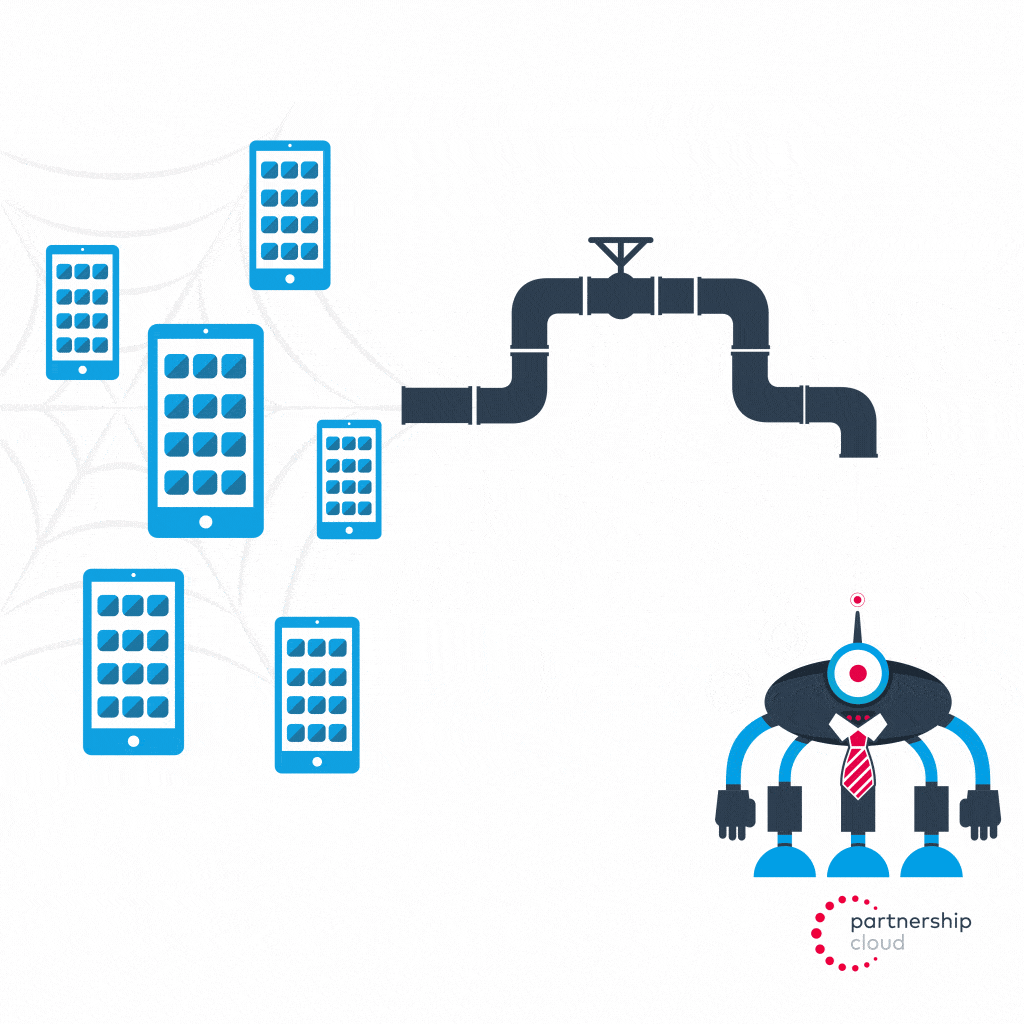
Install fraud
Inauthentic engagement
By way of paid human engagement farms or scripted retention, fraud scheme operators will enact or automate post-install engagement if that is the advertiser’s payable event. For example, the bad actor may navigate past a certain level in a game to simulate authentic user engagement.
How they do it
- Malicious publisher has registered for advertiser’s CPI campaign, which only rewards a partner for driving an install after user has leveled up in the app
- Malicious publisher sends proxied, automated traffic to a botnet of mobile devices
- Malicious publisher installs advertiser’s app on all botnet member devices
- Malicious publisher instructs botnet member devices to not just install advertiser’s app, but also to open the app and engage with the game up to the point of the first level-up
- Advertiser attributes credit to malicious publisher for every install that reached level one, even though all installs came from bots programmed to play the app